






























As the Internet of Everything (IoE) continues to drive one of the most sweeping market transitions in history, organizations will need to be hyper-aware, predictive, and agile. And IT will demand an infrastructure that is flexible...

The month of June was very exciting for FlexPod. On June 16th, Gartner released their 2014 Magic Quadrant for integrated infrastructure with FlexPod positioned in the leaders quadrant. On June 25th, Cisco and NetAppanno...

Noted business management author Peter Drucker famously said, "What's measured is improved." When applied to the world of security, meaningful security metrics can literally transform an organization and solve real business proble...

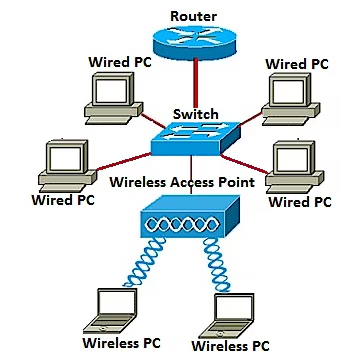
LiveAction 4.0, shipped in late June 2014, brings increased scalability to enable users the ability to see thousands of devices across their entire network on a single pane of glass. It provides centralized visibility and manageme...

I recently wrote a blog post about Steria, one of our Cisco Prime Service Catalog customers (you can also read their case study here). Today, I'm proud to introduce another case study on an IT service provider customer u...

(This is part 2 of a 7-part series sharing insights from Cisco partners about the Future of Cloud.) Chris Kemmerer, Director, Mobility Solutions, Verizon, had a lot to share with me at CiscoLive! "What I'm seeing this year is very...

Recently Sprinklr asked me how companies today are in trouble if they're not keeping up with social disruption. Which led me to consider: What makes a company smart when it comes to being social? Answer: Smart companie...

Today at Microsoft's Worldwide Partner Conference (WPC 2014) in Washington D.C. we entered into a new phase of our Microsoft relationship. Together Cisco and Microsoft announced a multi-year, worldwide sales and channel ...

The IT market is changing. Fast. As a result, customers expect their IT suppliers to offer capabilities beyond products and services, and deliveractualbusiness outcomes. That's why we're evolving the Cisco Partner Ecosystem. By ex...

Hurricane season is upon us, and storms have already begun to harass the Gulf Coast with torrential rains and violent winds. The threat of such a storm doesn't cross my mind as I sit in my cubicle in San Jose, enjoying the comfort...

Overview Phishing attacks use social engineering in an attempt to lure victims to fake websites. The websites could allow the attacker to retrieve sensitive or private information such as usernames, passwords, and credi...

This year's Cisco Live! was tremendous, with 25,000 attendees on-site and another 200,000 attending virtually. There was a lot of excitement around all things cloud, from how the Internet of Everything will change the way we...