




























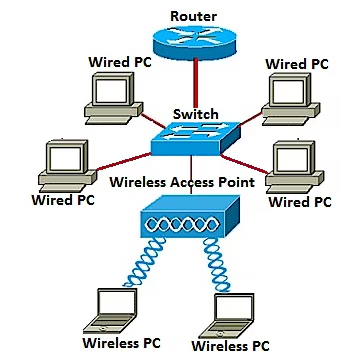


The Internet of Things (IoT) was a hot topic at Cisco Live last week in Milan. I got to spend a lot of time with customers, partners, and developers, and came home impressed by the tremendous focus on IoT applications. There is an...

Big data has become big business as businesses mine vast stores of data for insights that can help identify trends, predict behavior, and empower decision makers. And the Internet of Everything (IoE) is creating new analytic use c...

When I hear "hybrid" I think about cars. Those gas and electric cars that can switch to whichever power source is needed when it is needed the most or makes the most economical sense. The switch is, or at least should not be notic...

Given the tremendous interest in VXLAN with MP-BGP based EVPN Control-Plane (short EVPN) at Cisco Live in Milan, I decided to write a "short" technology brief blog post on this topic. VXLAN (IETF RFC7348) has been designed to s...

FlexPod had a great 2014 and continues to be a leader in the integrated infrastructure market. The collaboration and execution between the Cisco and NetApp teams have delivered the following results: Greater than 5,000 cus...

Security is a primary concern for many organizations making the transition to cloud. In the blog, "Taking a Hybrid Cloud Approach to Security", cloud provider Presidio shares how building a hybrid cloud enables you to maximi...

In an Internet of Everything era, enterprises and public sector organizations have developed an insatiable appetite for data. Data is being gathered from an increasing number of sources, and-from an analytics perspective-the more ...

We previously committed to providing important updates on our legal action over Arista's pervasive copying and misappropriation of Cisco intellectual property. Today, an International Trade Commission (ITC) Administrative Law Judg...

Guest Blog by Pat Chou, TMG Product Manager Since the introduction of the Cisco's 40G QSFP BiDi (Quad Small Form-Factor Pluggable Bidirectional module), we've seen phenomenal growth and adoption. I guess people do see the ben...

If you are involved in designing, supporting or managing a data center, you will undoubtedly rely on technical support services from one or more vendors. Running your data center, there is always the risk of a hardware failu...

OpenSOC, an open source security analytics framework, helps organizations make big data part of their technical security strategy by providing a platform for the application of anomaly detection and incident forensics to the data ...

Adversaries are committed to continually refining or developing new techniques to conceal malicious activity, decrease their reliance on other techniques that may be more detectable, and become increasingly more efficient and effe...