




























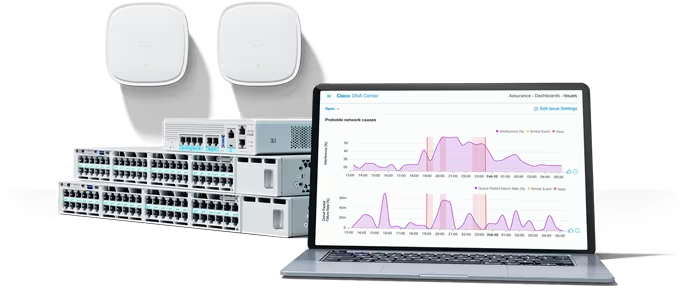


In this digital age, retailers' digital strategy and business strategy are becoming one as consumers increasingly expect a more customized shopping experience - one that provides value and convenience. Their expectations are highe...

There's a lot of hype around securing the Internet of Things (IoT). At the end of the day, I suggest that a more reasoned approach is in order. Securing the IoT will not be achieved by frantic worry about the volume of endpoints....

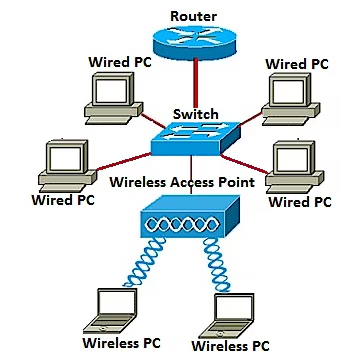
So, you've decided to introduce a collaboration solution to your organization. You've thought about the benefits you want it deliver: flexibility, expandability, and interoperability. And you want the user experience to be easy en...

Cloud computing is not a new concept for federal IT managers. The idea of transitioning to the cloud has been discussed, evaluated, loved and scrutinized for several years. There has and continues to be tremendous excitement about...

I recently attended the Strata + Hadoop World Conference in San Jose, and came away impressed with the accelerating pace of innovation in the world of Big Data. Companies and startups are innovating in every area of the Big Data v...

Earlier this month, I blogged about the challenges of Cloud Sprawl. Let's now turn to the challenges of "Application Sprawl"!If you are planning migration of applications inside or between data centers, or if you are plannin...

[Note: This is part 1 in a three part series of blogs discussing how Cisco ACI stands alone in the market. Part 2 | Part 3]| Part 3] Customers are bombarded by network virtualization and SDN technologies. In many cases, they are c...

Remember your first compact disc? Maybe yours was a music album like Billy Joel's "52nd Street" or Bruce Springsteen's "Born in the USA." Or maybe your first compact disc was the CD-ROM, used to download the first a...

Macro malware is a good example of malware writers and distributors using old tricks that most users have forgotten to spread malware. Unlike earlier macro malware, these macros don't infect other documents but download passw...

Kevin Collins, CEO and co-founder, Bit StewWe've introduced several of the key figures within Bit Stew and shared with you the ways they are working to bring the IIoTto fruition, particularly within the energy sector. I had a chat...

In 2001, Cisco Capital introduced Cisco Certified Refurbished Equipment (CCRE) a program designed to sell Cisco's high-quality refurbished products. To address the growing secondary market, and provide a price-competitive and trus...

At the recent Gartner BI Summit in Las Vegas, there was a lot of discussion about the paradigm shift underway in business intelligence (BI) and analytics. Business's need for agile data access and self-service, combined with IT's ...