






























The#ILookLikeAnEngineer hashtag is the diversity sensation that's sweeping the nations! The hashtag started as a way to break down stereotypes as to what an engineer might look like. It's not just nerdy guys. It's women, minoritie...

In a few weeks Spring season will set in, and it'll be a Ripper Down Under. For the Data Center technology geeks there is plenty of action in store to celebrate the onset of Aussie spring. I am talking about F5 Agility that is get...

Last week I wrote about how much we enjoyed talking with everyone who came to see us at Cisco Live as well as InfoComm, a conference with thousands of products from hundreds of exhibitors and more than 39,2015 attendees. It ...

Cisco UCS M-Series Modular Servers deliver exceptional value for online content delivery like gaming, web serving, transcoding, and HPC. Built around Cisco's virtual interface card (VIC) technology and the policy-based management ...

When we think of "cloud" we think of a vast collection of compute, network, and storage capabilities that resides somewhere high above us-a massive repository of functionality that can be accessed from anywhere and any device with...

What happens when more than 100 entrepreneurs embark on a 72-hour bus journey to concept, design and pitch the next big tech thing? With the right flow, pretty much anything they can imagine. StartupBus is one of the most unusual ...

Today's guest blog comes to us courtesy of Tesora CEO, Ken Rugg. The Cisco Intercloud is a pretty amazing demonstration of the power of OpenStack. It will have incredible worldwide reach with 350 data centers across 50 countries....

Coding errors in software products provide easy paths of entry for online criminals, who can exploit vulnerabilities to compromise systems or launch additional attacks and malware. As reported in theCisco 2015 Midyear Security Rep...

This post was authored by Mahdi Namazifar and Yuxi Pan Once a piece of malware has been successfully installed on a vulnerable system one of the first orders of business is for the malware to reach out to the remote command-and-co...

With the recent launch of FirePower Threat Defense on Cisco 4000 Series Integrated Services Routers, I would like to spend some time talking about enterprise branch security and what are the requirements to keep in mind to secure ...

If you had asked me a few years ago, I might have predicted that the rise of large scale hacking and network-based Advanced Persistent Threats (APTs) would spell the end of old-school espionage (poison-tipped umbrellas, office bre...

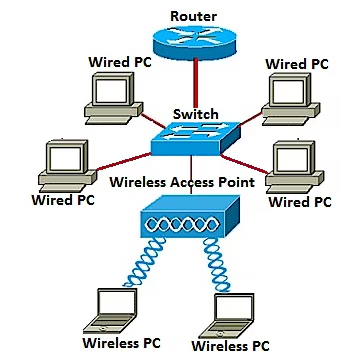
Only on TechWiseTVThis is the first in a multi-part series where we cover 'programmability' for networking. The idea is to fully review the programming options now available inside the Nexus switches, (3000, 9000). Thi...