






























Mobile security is a top concern for IT and business leaders.This blog series withDimension Dataexploreshow organizational leaders can work together to mitigate concern and implement clearly defined policies and mobility goals.Thi...

#CiscoChampion Radio is a podcast series by Cisco Champions as technologists, hosted by Cisco's Amy Lewis (@CommsNinja). This week Mike Korenbaum, Technical Marketing Engineer at Cisco, joins Cisco Champions Rick Vanover (@Ri...

In the wake of the European Parliament elections, stakeholders and commentators have been reflecting on the likely impact on important dossiers they follow. On data protection, we are pleased to welcome the reelection of the...

Written by Tom Davies, Technical Solutions Architect The world can be a tough place for a service provider in today's marketplace. Revenue per customer is declining and margins are shrinking. Over-the-top players are delivering s...

At Cisco Live, Hans Hwang, VP of Cisco Advanced Services spoke with Todd Walthall, Vice President, Digital Servicing Integration from American Express about how they are taking their customer service to the next level. By partneri...

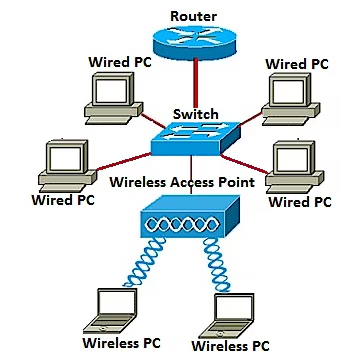
Everybody's talking about 802.11ac, but we've sensed some confusion for next steps as far as how CIO's and IT organizations should be approaching the new standard. Should I move to 802.11ac? You're probably thinking: Chris, you're...

The mobile market continues to evolve at a blindingly fast pace. It seems as though new faster, sleeker, and more powerful mobile devices are launched every day. And new categories of mobile devices are created almost overnight. T...

At the recent CiscoLive event in San Francisco, Soni Jiandani, Senior Vice President of Cisco INSBU, expanded on the industry momentum for Application Centric Infrastructure (ACI). She highlighted wide ranging customers and ...

Have you visited the DevNet portal website yet? DevNet is our new developer program, and the DevNet portal helps software developers build applications based on Cisco products- these apps can help you enhance and manage Cisc...

This post is co-authored by Martin Lee,Armin Pelkmann,and Preetham Raghunanda. Cyber security analysts tend to redundantly perform the same attack queries with different input data. Unfortunately, the search for useful meta-data c...

This blog post was written by Priscila David in collaboration with Emily Griffin, Anuja Singh and Rima Alameddine Today. Tomorrow. Transformed. This was the theme of the second annual Cisco Empo...

The 2014 Automation Conference (TAC) was held March 20-21, 2014 in sunny Chicago (Yes, sunny Chicago!! I made sure to pack some California sunshine for the Windy City) attracted a diverse group of automation and manufacturing thou...