







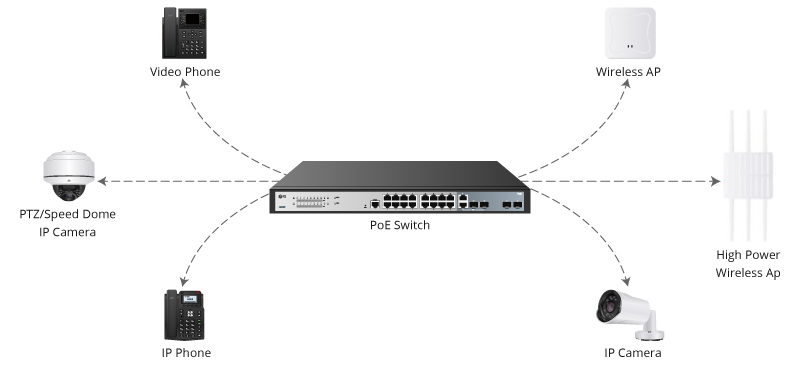







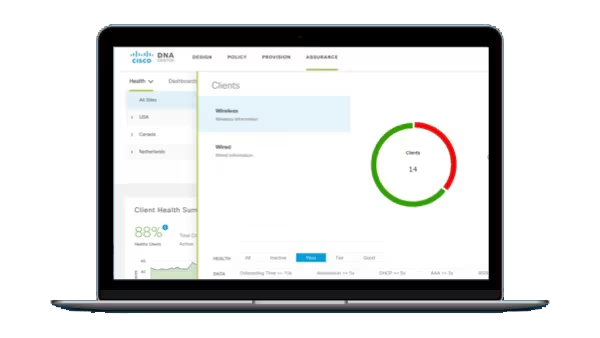

Endpoints, that is. After all, defense breaches, malware introduction, and security risks often arise from exploitation of endpoints such as user devices and smart things (IoT) connected to the network. And as organizations are going digital, their users are bringing in ever more devices, and their operations are adding IoT devices in record numbers, threats are likely only to increase.
Network administrators should take note. Some of these endpoints may have been added in an ad-hoc manner outside IT
 Etiquetas calientes:
Cisco DNA
Cisco DNA Center (en inglés)
Cisco SD-Access
#intentbasednetworking
AI Endpoint Analytics
Etiquetas calientes:
Cisco DNA
Cisco DNA Center (en inglés)
Cisco SD-Access
#intentbasednetworking
AI Endpoint Analytics