








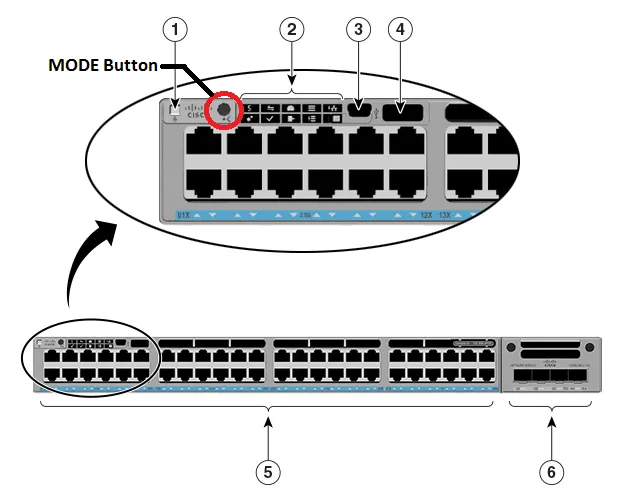







Cybersecurity researchers from JSOF have just published a set of 19 vulnerabilities, dubbed Ripple20 that are impacting the TCP/IP stack developed by Treck. This software stack is integrated into millions of systems used in the healthcare, transportation, manufacturing, telecoms and energy markets, potentially affecting a very large number of organizations and critical industries.
The vulnerabilities are similar to the Urgent/11 vulnerabilities published in 2019 and impacting the TCP/IP stack developed by Interpeak. Like Urgent/11, the Ripple20 vulnerabilities allow attackers to trigger remote code execution and denial of service (DoS). Many vendors such as HP, Schneider Electric, Intel, Rockwell Automation, Caterpillar, Baxter and others have already confirmed being impacted by Ripple20.
The Cisco IoT solutions designed for industrial environments are not affected by Ripple20. In fact, products like Cisco Cyber Vision and the Cisco Industrial Security Appliance ISA3000 together with Snort signatures from Cisco Talos will help identify Ripple20 vulnerabilities in your network and remediate risks. Some Cisco products are vulnerable, and you can read the official Cisco advisory here.
Treck was founded in 1997 and develops protocol stacks for real-time embedded systems. It is used by many equipment vendors as this software offers optimized performance for IoT devices that typically have limited memory or processing power for instance. It is sold in the form of a source code making it easy for vendors to integrate only the desired protocol layers and modify them for specific applications.
As a result, depending on how manufacturers have specialized and integrated these libraries, they can become virtually unidentifiable. In addition, as manufacturers have been acquired, some might have lost track of this software component, making it quite difficult
 Etiquetas calientes:
Internet of Things (IoT)
industria
Cisco Industrial IoT (IIoT)
ICS
IDS
Cisco Secure Industrial Networking
Cyber Vision
IoT Security Lab
isa3000
Etiquetas calientes:
Internet of Things (IoT)
industria
Cisco Industrial IoT (IIoT)
ICS
IDS
Cisco Secure Industrial Networking
Cyber Vision
IoT Security Lab
isa3000