


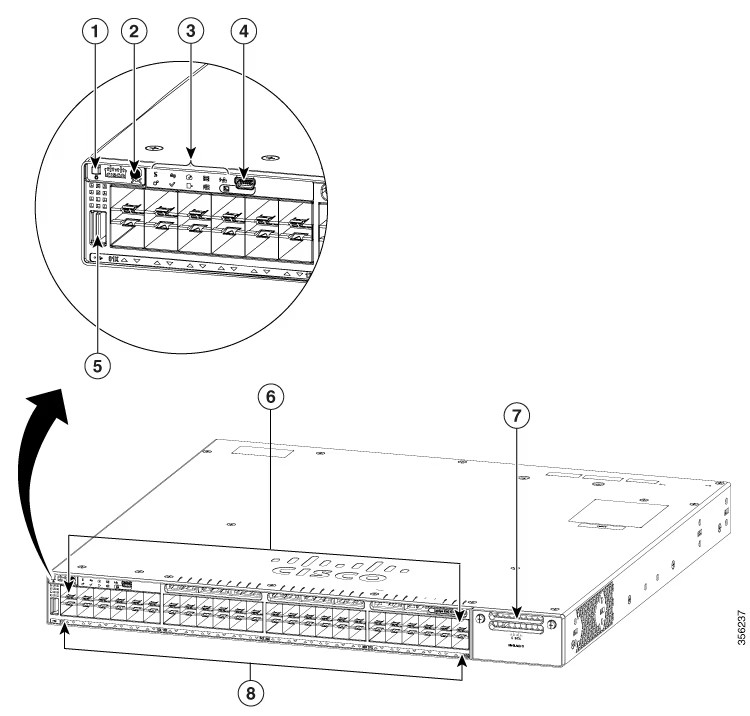












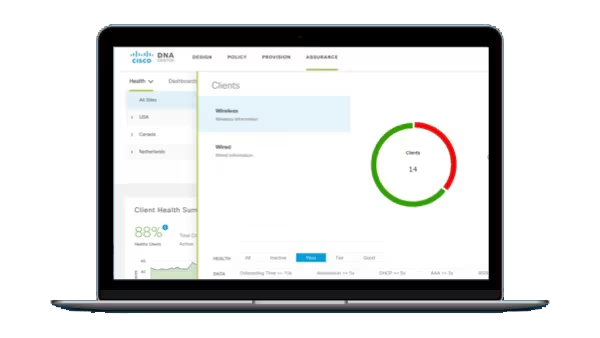

Businesses around the world have quickly moved to a remote worker initiative, with more users accessing critical workloads outside the traditional workplace than ever before. New attack vectors are inadvertently being introduced to businesses as users are accessing their workloads outside the traditional 4-walls of the workplace and the security protection those 4 walls provide.
To combat the uncertainty and risks introduced by mobilizing a greater than normal remote workforce, it is critical that IT maintains visibility into the network and application behavior from the source of both the users
 Etiquetas calientes:
destacado
Seguridad en la nube
Seguridad de aplicaciones
Application-First Security
Cisco Tetration
Cisco Secure Workload
Cloud Workload Security
Remote Work Security
Etiquetas calientes:
destacado
Seguridad en la nube
Seguridad de aplicaciones
Application-First Security
Cisco Tetration
Cisco Secure Workload
Cloud Workload Security
Remote Work Security