














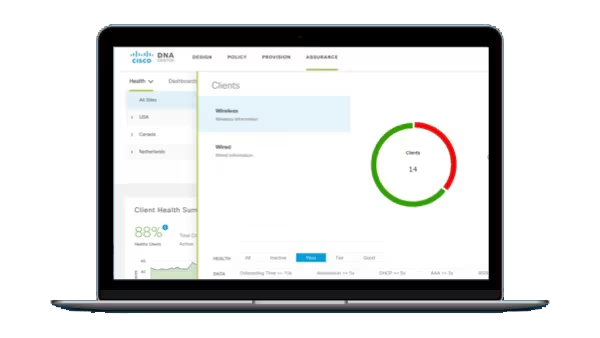
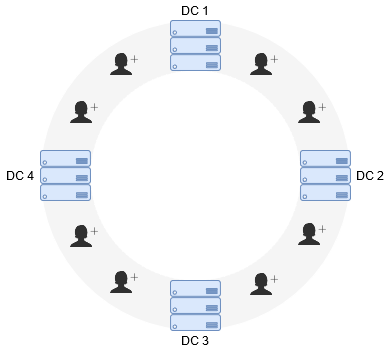

The erosion of the network perimeter has accelerated over the last year and this has changed the way we look at security. I wrote a blog about the emerging concept of a Secure Access Service Edge (SASE) architecture earlier this year and highlighted the core components that are required. In the past few months I haven
 Etiquetas calientes:
Cisco Meraki
Cisco SD-WAN
Cisco SASE
Cisco Partner Summit
Cisco Duo Security
Cisco AMP for Endpoints
casb
#CiscoPS20
AV-TEST
Etiquetas calientes:
Cisco Meraki
Cisco SD-WAN
Cisco SASE
Cisco Partner Summit
Cisco Duo Security
Cisco AMP for Endpoints
casb
#CiscoPS20
AV-TEST