































Complexity, opacity and the gatekeeping of knowledge are tactics often used to appear sophisticatedorintelligent. They can also be used to intimidate.
In security and technology, complexity can lead to critical gaps in visibility and an extended attack surface -with too many vendors and solutions to interconnect and manage. Additionally, many enterprises are operating with limited budgets, too many projects with conflicting priorities, projects creating disparity between different technology teams; all supported by a limited security team (or an IT or networking team doing double duty). As a result, complexity creep has risen to counteract our best security efforts.
At Cisco, we're seeking to eliminate that complexity and close knowledge gaps with simplicity in how we execute and deliver security, as well as transparency in how we talk about it. The security industry is often guilty of using buzzwords and jargon that can add to the growing complexity and shifting priorities as enterprises attempt to follow best security practices defined by the industry.
To that end, let's start with defining and simplifying the most popular buzzword, 'zero trust' -it's about never implicitly trusting, but always verifyingsomeone or somethingthat is requesting access to work resources.
It's not about getting rid of the perimeter -but rather tightening security on the inside.The new perimeter is less about the edge of the network, and now more about any place you make an access control decision.
-Wendy Nather, Head of Advisory CISOs, Summarized fromZero Trust: Going Beyond the Perimeter
Historically:
The new zero trust is about:
With all of that in mind,whatexactly are you trying to protect?
Enterprises are complex by nature. They have vast IT ecosystems, with many different vendors, software and infrastructure spread across the multi-cloud and on-premises. They have many different types of users -employees, contractors, customers, etc. -everywhere across the world -often using their own personal devices to work. They have applications that talk to each other via APIs, microservices and containers. And they still have enterprise networks that devices regularly access, including IoT.
That's why we've simplified things -by classifying each area of your enterprise IT as equally important to protect using a zero-trust security approach.
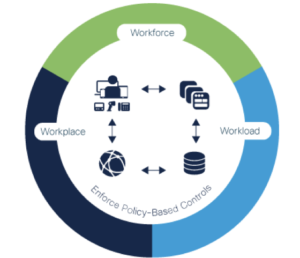
For complete zero-trust security, you need to address each area of your IT ecosystem -securing access across all environments, in a consistent and automated way.
Cisco's approach does not implicitly trust a request -but rather establishes trust for every access request, regardless of where the request is coming from. It secures access across your applications and network, while extending trust to support modern enterprises with BYOD, cloud apps and hybrid environments.
Cisco implements zero trust with a three-step methodology across the workforce, workloads and workplace by:
For the workforce, Duo Security protects against phishing, compromised credentials or other identity-based attacks with multi-factor authentication (MFA) to verify user identities and establish device trust before granting access to applications.
For workloads, Tetration secures hybrid, multi-cloud workloads and contains lateral movement with application segmentation. Identify vulnerabilities in software versions and block communication to reduce your overall attack surface.
For the workplace, Software-Defined Access (SD-Access) provides insight into users and devices, identify threats and provides control over all connections across the enterprise network, including IoT devices.
While this is a good starting place, other solutions in the Cisco Security portfolio can extend the zero-trust security model further. Cisco's framework is built to integrate seamlessly with your existing infrastructure and investments using an open API model, standards-based platform and strong technology partnerships to ensure that everything across your environment is protected -securing your enterprise as you scale.
Those strong partnerships include major players in the industry, including Microsoft, Amazon Web Services (AWS), Google and many more.Extending trust to integrate with third parties for better visibility and consistent policy enforcement is key to making a zero-trust approach practical and effective for modern enterprises.
Overall -this framework provides the benefits of a comprehensive zero-trust approach:
Learn more about Cisco Zero Trust. Or, sign up for a free trial of Duo, demo Tetration and learn more about SD-Access to start your zero-trust journey today.
Did you hear? Cisco was named a leader inThe Forrester Wave?: Zero Trust eXtended Ecosystem Platform Providers, Q4 2019-read the report.
 Etiquetas calientes:
Cisco Duo Security
Cisco Zero Trust
SD-Access
tetration
zero trust security
Etiquetas calientes:
Cisco Duo Security
Cisco Zero Trust
SD-Access
tetration
zero trust security