



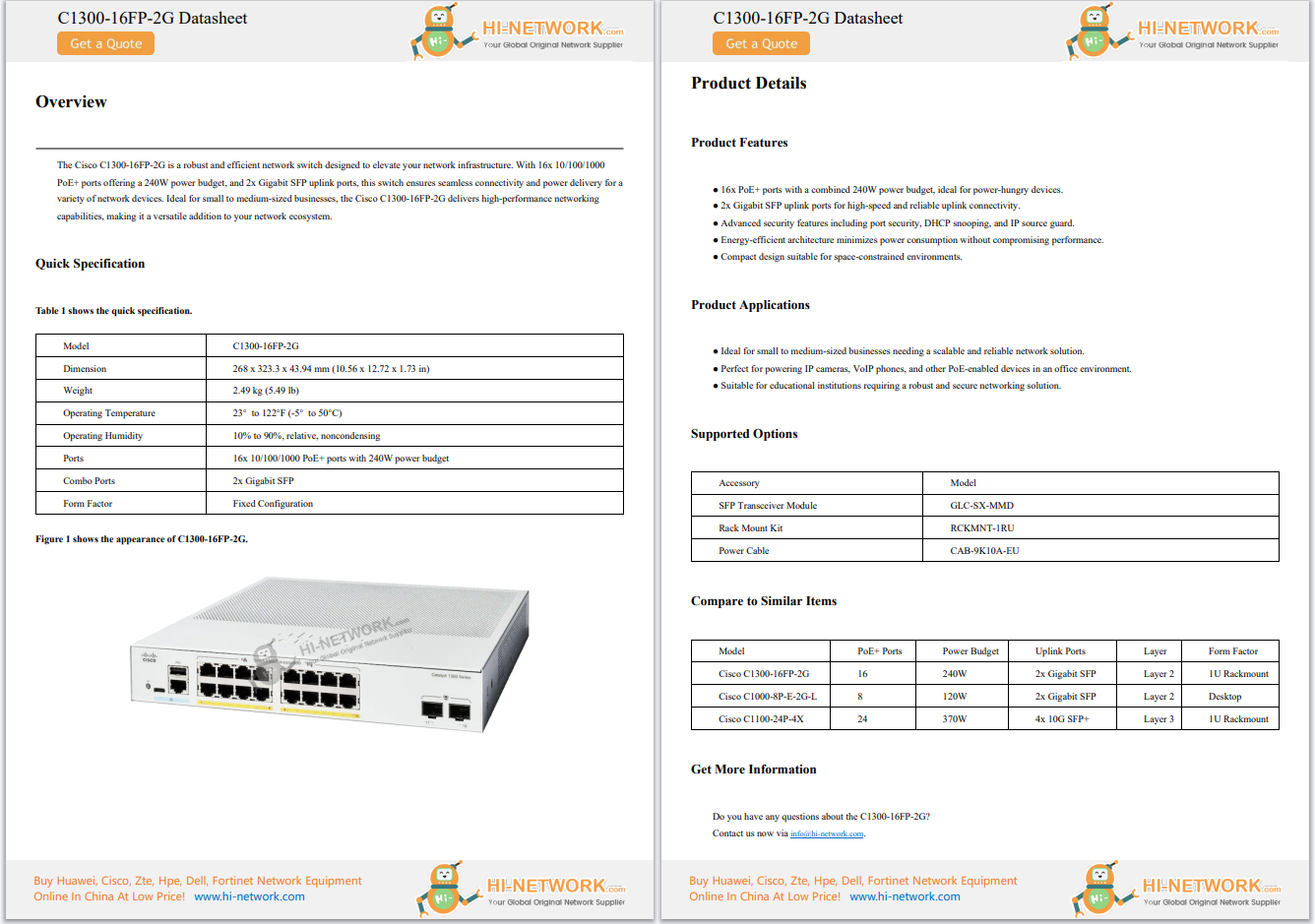












In recent weeks, the occurrence of brute force login attempts targeting WordPress and Joomla installations have significantly increased in volume, with some entities reporting triple the attempts seen in the past. The attack volume has been so severe that it has led some hosting providers to block all attempts to access wp-login.php, even for site owners or administrators. While blocking all access outright might seem a bit draconian, about 25% of websites globally include WordPress installations -a tremendous attack surface if left undefended.
During the course of its investigation, Cisco TRAC discovered a repository of data believed to potentially be feeding the brute force login attempts. The trove included user lists, site lists, and password lists. Additionally, there is a list that appears to be a compilation of usernames and passwords used in previous brute force login attempts, scrapings from phishing and cracking forums, as well as the Nmap password list of common passwords. The compiled list has over 25,000 entries, half of which were duplicates. After cleaning up the duplicates, we were left with 783 unique usernames and 11,001 unique passwords -resulting in over 8.6 million possible combinations. However, it doesn't appear the attackers are going to that extent; the total list of username/password pairs (with dupes removed) contained just over 13,000 combinations.
Examples of some of the more complex passwords discovered include:
In addition to these, other login attempts will include usernames and passwords derived from the site name. For example, a brute force login attempt on example.com might include any or all of the following:
The repository upon which these linked lists were found also included links to pages containing the type of 'feed' information that would be useful for spamdexing or generating nonsensical verbiage designed to bypass content filters for email and comment spam.
In addition to attempting to determine the source of the materials used in the attacks, we were also interested in trying to determine what tools might be used to facilitate the seemingly automated brute force login attempts. Although as many as 90,000 unique IP addresses have been reportedly used in the attacks, other characteristics seemed to point not to a botnet of infected machines but rather a potential small handful of individuals.
Working from the known characteristics, Cisco TRAC has been able to identify at least three tools capable of these widespread brute force login attempts. Through the use of any one of these tools, attackers simply need to specify the source location for a username list, password list, and site list, as well as designating the sending proxy (which would certainly explain the 90,000 unique IP addresses that have been reported).
IP spoofing has also been reported in the WordPress and Joomla brute force attacks and indeed there are bonafide victim logs reflecting brute force login attempts from DNS servers and other legitimate, non-attacking addresses. However, this 'spoofing' most likely results from the attacker simply specifying an arbitrary value for the X-Forwarded-For header. Assuming this theory is correct, this indicates more of a problem with the logging service blindly accepting the declared value versus any actual spoofing of the TCP connection for the HTTP transaction.
At least in some cases, following successful brute forcing of the username and password, attackers are uploading a PHP shell to the newly compromised site, creating a staging area in an attacker-added folder named pwksfmaw:

An example of malware that employs this structure:
Malware employing other brute forced WordPress sites:
Note that this is a partial list only.
We'll end this blog post with a brief wrap-up. We believe attackers are combining residual username and password lists found in wp-content/uploads/data.txt of previously compromised sites. These lists are combined with other sources, resulting in a master list comprising over 8.6 million possible combinations. Despite the 90,000 unique IPs, the source of the attacks is probably not the work of a botnet, but rather the work of a few individuals who are using one of these automated web-based, password-cracking tools and masquerading the source of their brute force login attempts through the use of an open proxy. Any semblance of IP spoofing is likely a result of a forged X-Forwarded-For header. Upon successful compromise, attackers upload a PHP shell and create a folder/malware structure used to facilitate other in-progress attacks.
Joseph Karpenko, Strategic Security Researcher for Cisco, helped investigate and contributed to this post.
 Etiquetas calientes:
Cisco Security
TRAC
brute force login
WordPress
Joomla Brute Force
Etiquetas calientes:
Cisco Security
TRAC
brute force login
WordPress
Joomla Brute Force